Refer to the exhibit.
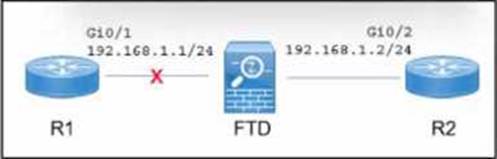
A Cisco Secure Firewall Threat Defense (FTD) device is deployed in inline mode with an inline set. The network engineer wants router R2 to remove the directly connected route M 68.1.0/24 from its routing table when the cable between routed R1 and the Secure FTD device Is disconnected.
Which action must the engineer take?
A. Implement the Propagate Link Stale option on the Secure FTD device
B. Establish a routing protocol between R1 and R2.
C. Disable hardware bypass on the Secure FTD device.
D. Implement autostate functionality on the Gi0/2 interface of R2
Explanation:
To ensure that router R2 removes the directly connected route for 192.168.1.0/24 from its routing table when the cable between router R1 and the Secure FTD device is disconnected, the network engineer must implement the "Propagate Link State" option on the Secure FTD device. This option allows the FTD to propagate the link state changes to adjacent devices, ensuring that the disconnection is recognized and the routing table is updated accordingly.
Steps:
Access the FTD device configuration via FMC.
Navigate to the interface settings for the relevant interfaces.
Enable the "Propagate Link State" option for the interfaces connected to R1 and R2.
Deploy the changes to the FTD device.
This configuration ensures that the link state changes are communicated to router R2, prompting it to remove the disconnected route from its routing table.
Reference: Cisco Secure Firewall Threat Defense Configuration Guide, Chapter on Interface Settings and Link State Propagation.