Refer to the exhibits.
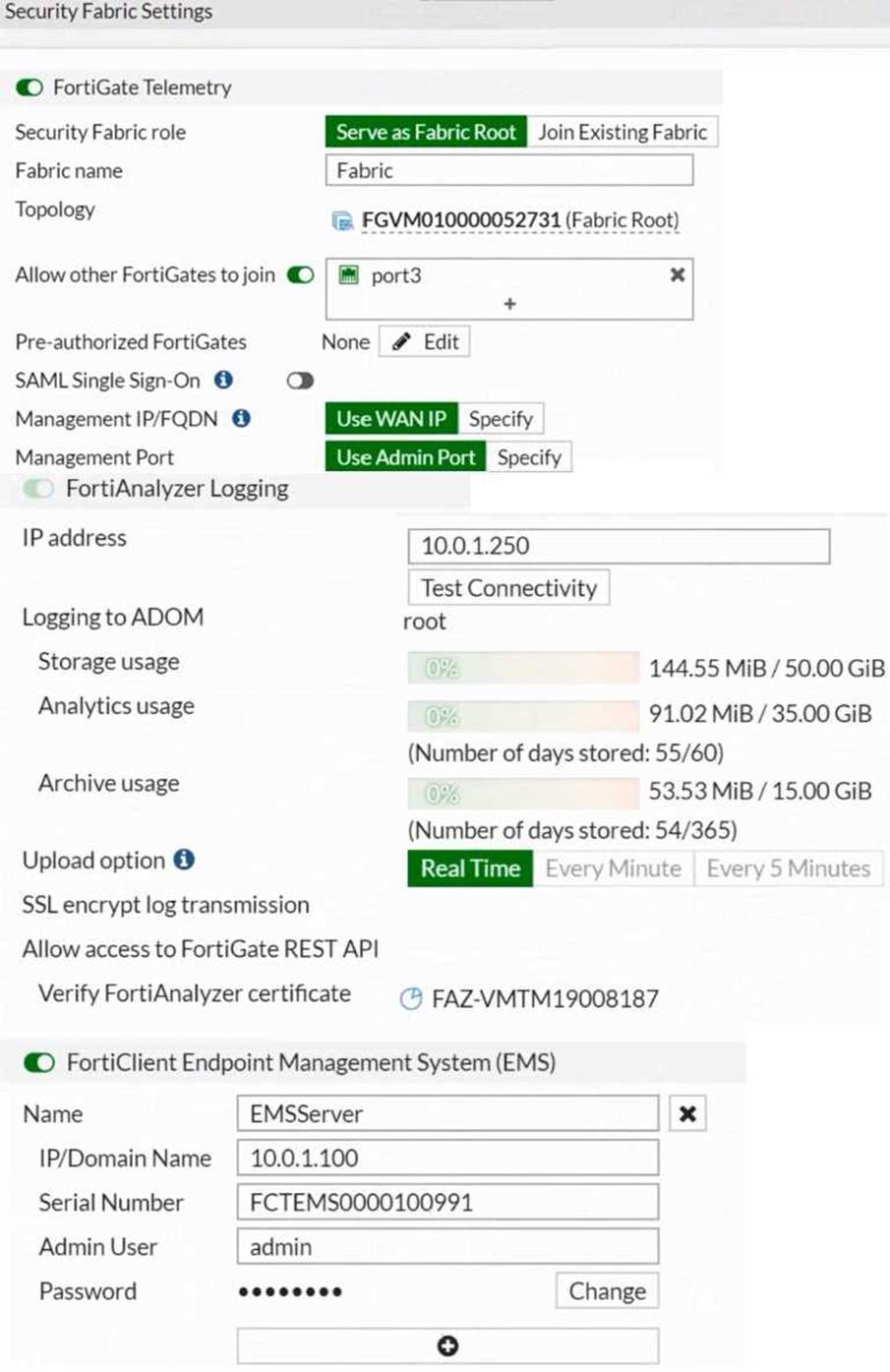
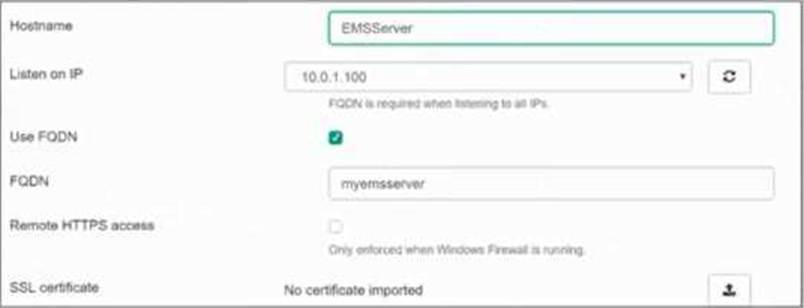
Based on the FortiGate Security Fabric settings shown in the exhibits, what must an administrator do on the EMS server to successfully quarantine an endpoint.
When it is detected as a compromised host (loC)?
A. The administrator must enable remote HTTPS access to EM
B. The administrator must enable FQDN on EM
C. The administrator must authorize FortiGate on FortiAnalyzer.
D. The administrator must enable SSH access to EM
Explanation:
Based on the FortiGate Security Fabric settings shown in the exhibits, to successfully quarantine an endpoint when it is detected as a compromised host (IOC), the following step is required:
Enable Remote HTTPS Access to EMS: This setting allows FortiGate to communicate securely with FortiClient EMS over HTTPS. Remote HTTPS access is essential for the quarantine functionality to operate correctly, enabling the EMS server to receive and act upon the quarantine commands from FortiGate.
Therefore, the administrator must enable remote HTTPS access to EMS to allow the quarantine process to function properly.
Reference
FortiGate Infrastructure 7.2 Study Guide, Security Fabric and Integration with EMS Sections Fortinet Documentation on Enabling Remote HTTPS Access to FortiClient EMS